S
Size: a a a
2019 October 31
привет всем,кто нибудь подсказать сможет какие примерно должностные обязанности у инженера системы SCADA ?
AK
привет всем,кто нибудь подсказать сможет какие примерно должностные обязанности у инженера системы SCADA ?
Спроси здесь t.me/ru_ASUTP
S
SK
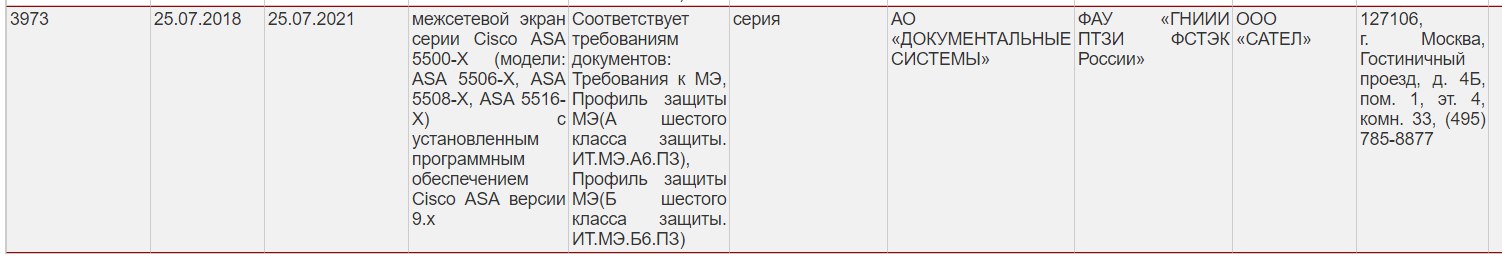
а как насчет профиля защиты систем обнаружения вторжений уровня сети четвертого класса защиты?
SK
и почему шестого класса защиты?
E
а как насчет профиля защиты систем обнаружения вторжений уровня сети четвертого класса защиты?
E
и почему шестого класса защиты?
не понял вопроса
AS

Перед вами кульминация 3х дней стараний True0xA3 на Standoff в Абу-Даби и основная причина их победы. Демонстрация APT как она есть. Что может быть страшнее для людей в Эмиратах, чем неконтролируемый разлив нефти...
2019 November 01
NK
«Элтеза», дочерняя компания РЖД, внедряет вычислительные комплексы на базе защищенной отечественной программно-аппаратной платформы «Эльбрус» в системы управления движением поездов.
https://www.cnews.ru/news/top/2019-10-31_rossijskie_sistemy_upravleniya
https://www.cnews.ru/news/top/2019-10-31_rossijskie_sistemy_upravleniya
NK
NK
Новый документ SANS об анализе протокола BACnet, включая парсер для системы мониторинга Zeek/Bro: Guarding the Modern Castle: Providing Visibility into the BACnet Protocol
https://www.sans.org/reading-room/whitepapers/ICS/paper/39240
https://www.sans.org/reading-room/whitepapers/ICS/paper/39240
NK
KICS con 2019: Интервью с Владимиром Дащенко (Лаборатория Касперского)
Почему bug bounty необходимо внедрять в мире промышленных систем — объясняет специалист «Лаборатории Касперского».
https://youtu.be/zjiohFsGlHA
Почему bug bounty необходимо внедрять в мире промышленных систем — объясняет специалист «Лаборатории Касперского».
https://youtu.be/zjiohFsGlHA
NK
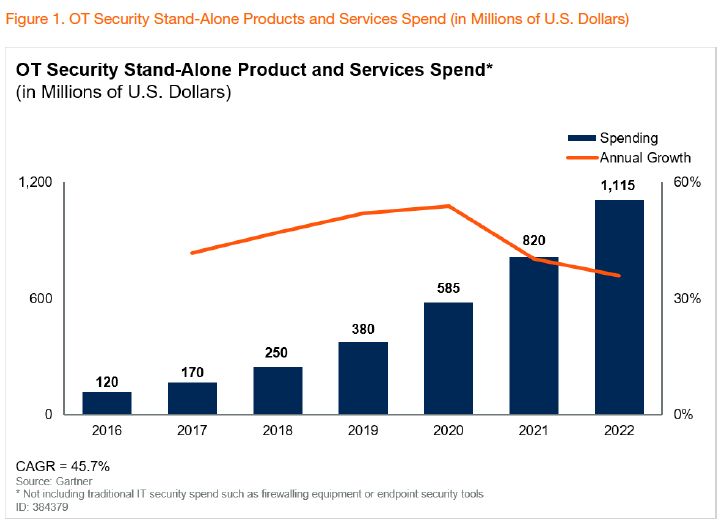
В августе Gartner опубликовал новый отчет: "Best Practices for Security Providers to Take Advantage of Growing OT-Related Opportunities"
Отчет доступен по подписке. Но вот интересный фрагмент оттуда: прогноз глобального рынка OT Security по мнению Gartner
https://www.gartner.com/en/documents/3956240
Отчет доступен по подписке. Но вот интересный фрагмент оттуда: прогноз глобального рынка OT Security по мнению Gartner
https://www.gartner.com/en/documents/3956240
AL
NK
IMPROPER LIMITATION OF A PATHNAME TO A RESTRICTED DIRECTORY ('PATH TRAVERSAL') CWE-22
Path traversal vulnerabilities are caused by a lack of proper validation of a user-supplied path prior to use in file operations. An attacker can leverage these vulnerabilities to remotely execute code while posing as an administrator.
MISSING AUTHORIZATION CWE-862
There is an unsecured function that allows anyone who can access the IP address to use the function without authentication.
IMPROPER RESTRICTION OF XML EXTERNAL ENTITY REFERENCE CWE-611
XXE vulnerabilities exist that may allow disclosure of sensitive data.
IMPROPER NEUTRALIZATION OF SPECIAL ELEMENTS USED IN AN SQL COMMAND ('SQL INJECTION') CWE-89
Lack of sanitization of user-supplied input cause SQL injection vulnerabilities. An attacker can leverage these vulnerabilities to disclose information.
https://www.us-cert.gov/ics/advisories/icsa-19-304-01
Path traversal vulnerabilities are caused by a lack of proper validation of a user-supplied path prior to use in file operations. An attacker can leverage these vulnerabilities to remotely execute code while posing as an administrator.
MISSING AUTHORIZATION CWE-862
There is an unsecured function that allows anyone who can access the IP address to use the function without authentication.
IMPROPER RESTRICTION OF XML EXTERNAL ENTITY REFERENCE CWE-611
XXE vulnerabilities exist that may allow disclosure of sensitive data.
IMPROPER NEUTRALIZATION OF SPECIAL ELEMENTS USED IN AN SQL COMMAND ('SQL INJECTION') CWE-89
Lack of sanitization of user-supplied input cause SQL injection vulnerabilities. An attacker can leverage these vulnerabilities to disclose information.
https://www.us-cert.gov/ics/advisories/icsa-19-304-01
A
Offensive Security Advanced Web Attacks and Exploitation VMs Lab v2016