AS
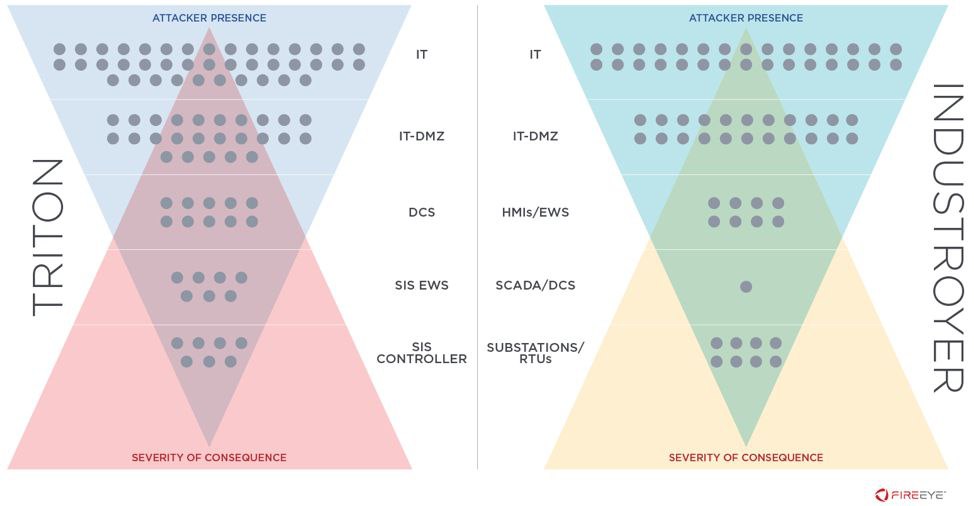
The Theory of 99: Almost All Threat Activity Happens in Windows and Linux Systems
99% of compromised systems will be computer workstations and servers
99% of malware will be designed for computer workstations and servers
99% of forensics will be performed on computer workstations and servers
99% of detection opportunities will be for activity connected to computer workstations and servers
99% of intrusion dwell time happens in commercial off-the-shelf (COTS) computer equipment before any Purdue level 0-1 devices are impacted
https://www.fireeye.com/blog/threat-research/2019/12/fireeye-approach-to-operational-technology-security.html