И
Size: a a a
2021 March 03
У моих заказчиков проблем нет
Угу спс Виктория
AG
У моих заказчиков проблем нет
я не твой заказчик но у меня тоже все збс)
AG
AG
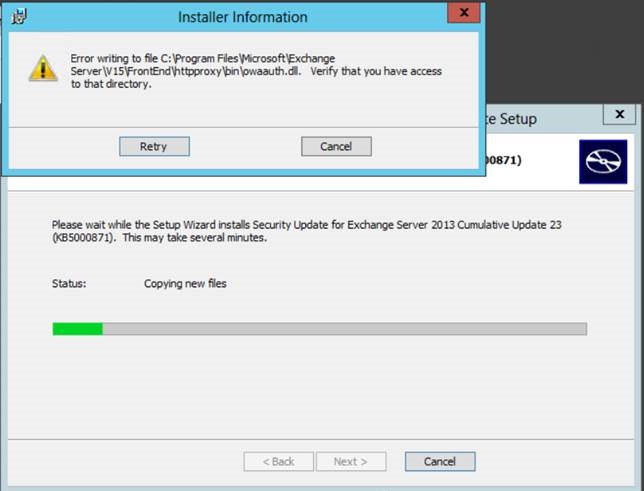
там в комментах прикольно) чел ецп сломал себе запустив по двойному клику обновку)😂
m
там в комментах прикольно) чел ецп сломал себе запустив по двойному клику обновку)😂
ну мало кто читает че мс советует при установке
AG
ну мало кто читает че мс советует при установке
да я просто не понимаю, как так можно, читать блог и не читать про обновку
m
да я просто не понимаю, как так можно, читать блог и не читать про обновку
а я не понимаю когда человеку формализованную инструкцию даешь из 3 шагов, а он и этого сделать не может. вот не читает и все. и частенько таких встречаешь
VG
там в комментах прикольно) чел ецп сломал себе запустив по двойному клику обновку)😂
По обновлениям -
Updates for customers - important to know
As stated in the patch download, install the update from an elevated CMD, otherwise some files are not correctly updated. Do NOT simply double-click the patch
https://support.microsoft.com/en-us/topic/description-of-the-security-update-for-microsoft-exchange-server-2019-2016-and-2013-march-2-2021-kb5000871-9800a6bb-0a21-4ee7-b9da-fa85b3e1d23b
In some cases the update does not ask for a reboot after installation. Always reboot when the installation has finished
Can I determine if I have been compromised by this activity?
The script at https://www.microsoft.com/security/blog/2021/03/02/hafnium-targeting-exchange-servers/ has a typo, here is the corrected version
Import-Csv -Path (Get-ChildItem -Recurse -Path “$env:PROGRAMFILES\Microsoft\Exchange Server\V15\Logging\HttpProxy” -Filter ‘*.log’).FullName | Where-Object { $_.AuthenticatedUser -eq "" -and $_.AnchorMailbox -like ‘ServerInfo~*/*’ } | select DateTime, AnchorMailbox
Ну и читайте таки ридми.
Updates for customers - important to know
As stated in the patch download, install the update from an elevated CMD, otherwise some files are not correctly updated. Do NOT simply double-click the patch
https://support.microsoft.com/en-us/topic/description-of-the-security-update-for-microsoft-exchange-server-2019-2016-and-2013-march-2-2021-kb5000871-9800a6bb-0a21-4ee7-b9da-fa85b3e1d23b
In some cases the update does not ask for a reboot after installation. Always reboot when the installation has finished
Can I determine if I have been compromised by this activity?
The script at https://www.microsoft.com/security/blog/2021/03/02/hafnium-targeting-exchange-servers/ has a typo, here is the corrected version
Import-Csv -Path (Get-ChildItem -Recurse -Path “$env:PROGRAMFILES\Microsoft\Exchange Server\V15\Logging\HttpProxy” -Filter ‘*.log’).FullName | Where-Object { $_.AuthenticatedUser -eq "" -and $_.AnchorMailbox -like ‘ServerInfo~*/*’ } | select DateTime, AnchorMailbox
Ну и читайте таки ридми.
AG
По обновлениям -
Updates for customers - important to know
As stated in the patch download, install the update from an elevated CMD, otherwise some files are not correctly updated. Do NOT simply double-click the patch
https://support.microsoft.com/en-us/topic/description-of-the-security-update-for-microsoft-exchange-server-2019-2016-and-2013-march-2-2021-kb5000871-9800a6bb-0a21-4ee7-b9da-fa85b3e1d23b
In some cases the update does not ask for a reboot after installation. Always reboot when the installation has finished
Can I determine if I have been compromised by this activity?
The script at https://www.microsoft.com/security/blog/2021/03/02/hafnium-targeting-exchange-servers/ has a typo, here is the corrected version
Import-Csv -Path (Get-ChildItem -Recurse -Path “$env:PROGRAMFILES\Microsoft\Exchange Server\V15\Logging\HttpProxy” -Filter ‘*.log’).FullName | Where-Object { $_.AuthenticatedUser -eq "" -and $_.AnchorMailbox -like ‘ServerInfo~*/*’ } | select DateTime, AnchorMailbox
Ну и читайте таки ридми.
Updates for customers - important to know
As stated in the patch download, install the update from an elevated CMD, otherwise some files are not correctly updated. Do NOT simply double-click the patch
https://support.microsoft.com/en-us/topic/description-of-the-security-update-for-microsoft-exchange-server-2019-2016-and-2013-march-2-2021-kb5000871-9800a6bb-0a21-4ee7-b9da-fa85b3e1d23b
In some cases the update does not ask for a reboot after installation. Always reboot when the installation has finished
Can I determine if I have been compromised by this activity?
The script at https://www.microsoft.com/security/blog/2021/03/02/hafnium-targeting-exchange-servers/ has a typo, here is the corrected version
Import-Csv -Path (Get-ChildItem -Recurse -Path “$env:PROGRAMFILES\Microsoft\Exchange Server\V15\Logging\HttpProxy” -Filter ‘*.log’).FullName | Where-Object { $_.AuthenticatedUser -eq "" -and $_.AnchorMailbox -like ‘ServerInfo~*/*’ } | select DateTime, AnchorMailbox
Ну и читайте таки ридми.
это ты к чему?)
AG
это ты к чему?)
в бложке команды все эти ссылки же приведены)
AG
после того как исходники улетели, я думаю мы таких дырок много еще закрывать будем)
MS
Mikhail Novoseltsev
Так если не проблема поднять) и нет айдентити то надо пользоваться)
Чем? Я не понял:(
m
после того как исходники улетели, я думаю мы таких дырок много еще закрывать будем)
даешь кумулятивы каждый месяц
AG
даешь кумулятивы каждый месяц
так щас вышла же секурная а не комулятивка, комулятивки как и были раз в 3 месяца, а вот секурные думаю еще нираз увидим
VG
это ты к чему?)
Может кто прочитает, перестанет себе ECP ломать
m
так щас вышла же секурная а не комулятивка, комулятивки как и были раз в 3 месяца, а вот секурные думаю еще нираз увидим
так там в статье ж пишут что в мартовский ку включат все секьюры
AG
Может кто прочитает, перестанет себе ECP ломать
так это не сюда) это надо в коммент челу написать в бложик)
AG
так там в статье ж пишут что в мартовский ку включат все секьюры
это понятно, но вот например для 16 комулятивка мартовская скорей всего последняя будет)
AG
это понятно, но вот например для 16 комулятивка мартовская скорей всего последняя будет)
ну или мб еще одна когда-нить выйдет) соберет все секурные обновки в себя в промежутках)
АТ
По обновлениям -
Updates for customers - important to know
As stated in the patch download, install the update from an elevated CMD, otherwise some files are not correctly updated. Do NOT simply double-click the patch
https://support.microsoft.com/en-us/topic/description-of-the-security-update-for-microsoft-exchange-server-2019-2016-and-2013-march-2-2021-kb5000871-9800a6bb-0a21-4ee7-b9da-fa85b3e1d23b
In some cases the update does not ask for a reboot after installation. Always reboot when the installation has finished
Can I determine if I have been compromised by this activity?
The script at https://www.microsoft.com/security/blog/2021/03/02/hafnium-targeting-exchange-servers/ has a typo, here is the corrected version
Import-Csv -Path (Get-ChildItem -Recurse -Path “$env:PROGRAMFILES\Microsoft\Exchange Server\V15\Logging\HttpProxy” -Filter ‘*.log’).FullName | Where-Object { $_.AuthenticatedUser -eq "" -and $_.AnchorMailbox -like ‘ServerInfo~*/*’ } | select DateTime, AnchorMailbox
Ну и читайте таки ридми.
Updates for customers - important to know
As stated in the patch download, install the update from an elevated CMD, otherwise some files are not correctly updated. Do NOT simply double-click the patch
https://support.microsoft.com/en-us/topic/description-of-the-security-update-for-microsoft-exchange-server-2019-2016-and-2013-march-2-2021-kb5000871-9800a6bb-0a21-4ee7-b9da-fa85b3e1d23b
In some cases the update does not ask for a reboot after installation. Always reboot when the installation has finished
Can I determine if I have been compromised by this activity?
The script at https://www.microsoft.com/security/blog/2021/03/02/hafnium-targeting-exchange-servers/ has a typo, here is the corrected version
Import-Csv -Path (Get-ChildItem -Recurse -Path “$env:PROGRAMFILES\Microsoft\Exchange Server\V15\Logging\HttpProxy” -Filter ‘*.log’).FullName | Where-Object { $_.AuthenticatedUser -eq "" -and $_.AnchorMailbox -like ‘ServerInfo~*/*’ } | select DateTime, AnchorMailbox
Ну и читайте таки ридми.
На вскидку - нормальный вариант команды проверки логов, без единовременного засовывания их всех в память... Возможно не пашет, толком еще не проверил.
Get-ChildItem -Recurse -Path "$env:PROGRAMFILES\Microsoft\Exchange Server\V15\Logging\HttpProxy" -Filter '*.log'| ForEach {Import-Csv -Path $_.FullName| Where-Object { $_.AuthenticatedUser -eq "" -and $_.AnchorMailbox -like 'ServerInfo~*/*' } | select DateTime, AnchorMailbox }
Get-ChildItem -Recurse -Path "$env:PROGRAMFILES\Microsoft\Exchange Server\V15\Logging\HttpProxy" -Filter '*.log'| ForEach {Import-Csv -Path $_.FullName| Where-Object { $_.AuthenticatedUser -eq "" -and $_.AnchorMailbox -like 'ServerInfo~*/*' } | select DateTime, AnchorMailbox }