AK
Size: a a a
2020 October 15
где пруфы
https://tpm.fail ну и вообще опираться на security through obscurity на таких важных штуках нельзя, а почти все реализации не опенсорсные. еще вроде в снапдрагоне какое-то время назад похожую штуку жутко поломали. + если что-то найдут в будущем, то починить это апгрейдом с вероятностью 99% будет нельзя
v
https://tpm.fail ну и вообще опираться на security through obscurity на таких важных штуках нельзя, а почти все реализации не опенсорсные. еще вроде в снапдрагоне какое-то время назад похожую штуку жутко поломали. + если что-то найдут в будущем, то починить это апгрейдом с вероятностью 99% будет нельзя
по ссылке не очень понятно, подделывать подписи? это как-то поможет с битлокером, например?
AK
по ссылке не очень понятно, подделывать подписи? это как-то поможет с битлокером, например?
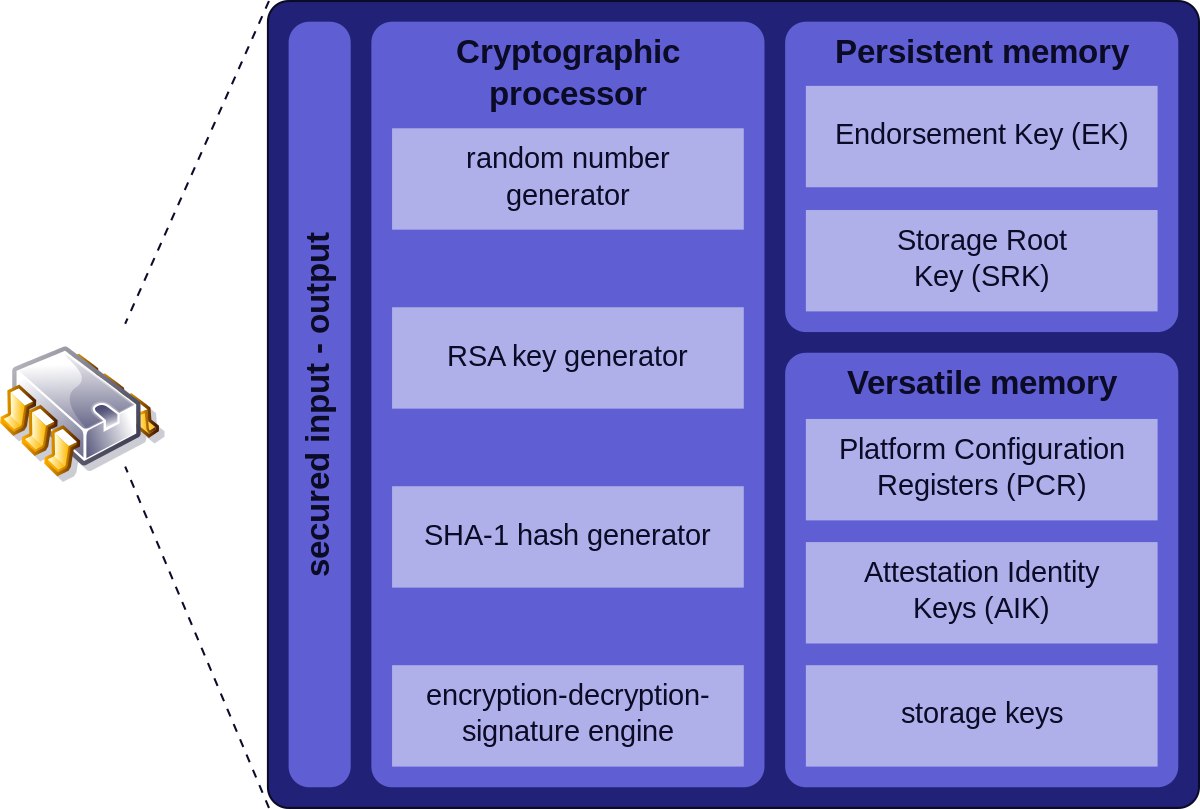
The research team says the "timing leakage" they discovered can be used to extract 256-bit private keys that are being stored inside the TPM. More specifically, 256-bit private keys used by certain digital signature schemes based on elliptic curves algorithms such as ECDSA and ECSchnorr.
AK
https://ironpeak.be/blog/crouching-t2-hidden-danger/ вот кстати про яббл, это вообще эпично-эталонно и поражение