IP
Size: a a a
2021 May 13
На эту тему есть еще свежее:
IP

SP
Шрифт из детства
NK
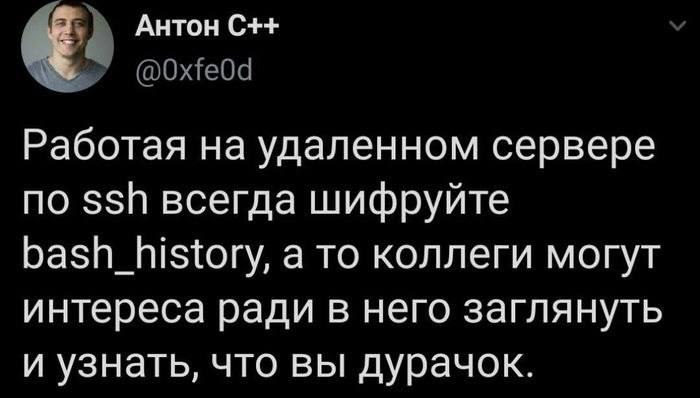
С
Хахахахха
SK
Жиза
NH
ору)
N
ключ від ссш не пишеться в історію вроді як
s
Так тут і не про ключ
N
про історію команд?
И
Можно просто коллеге подбросить свои логи
И
Глядиш ещё и посадют
B
Подбросить логи где ты подбрасываешь логи
И
На улице
N
Whom are you hiding your history from?
Is it an attacker must have access to your home directory and can read your "dot" configuration files and other material. Why don't you just use permissions to keep them out?
Is the attacker an administrator, not kept out by permissions? (Either has root, or unfettered access to system backups that contain your home directory and so on.) In that case, why specifically worry about your Bash history? You have no privacy on that system. The attacker can spy on the memory in your running processes.
Is your machine locally secured (accessible only by you), but your home directory is mounted on a networked file system? In that case, why don't you use an encrypted file system layer over that networked mount, so that all your files are protected together, not just your Bash history.
As you can see, there is hardly any use case for the whack-a-mole approach to file security (leaving it to each individual application to protect specific files).
Is it an attacker must have access to your home directory and can read your "dot" configuration files and other material. Why don't you just use permissions to keep them out?
Is the attacker an administrator, not kept out by permissions? (Either has root, or unfettered access to system backups that contain your home directory and so on.) In that case, why specifically worry about your Bash history? You have no privacy on that system. The attacker can spy on the memory in your running processes.
Is your machine locally secured (accessible only by you), but your home directory is mounted on a networked file system? In that case, why don't you use an encrypted file system layer over that networked mount, so that all your files are protected together, not just your Bash history.
As you can see, there is hardly any use case for the whack-a-mole approach to file security (leaving it to each individual application to protect specific files).
MH
К чему это?)
s
Сказано ж, дізнаються що ти дурачок
NK

В официальном аккаунте киберкопов в ФБ опубликовали следующее: "Сотрудники киберполиции улучшили знания и практические навыки по OSINT для эффективного расследования киберпреступлений
Лекцию и тренинги для правоохранителей провел специалист по кибербезопасности Никита Кныш" (на фото справа, рядом с начальником всея киберполиции А. Гринчаком). "По результатам было улучшено методику выявления и идентификации кибер-злоумышленников".
Короче, улучшили и обязательно углубили. Осталось расширить и смазать. Никита, а не западло копам рассказывать как "кибер-злоумышленников" палить?
Лекцию и тренинги для правоохранителей провел специалист по кибербезопасности Никита Кныш" (на фото справа, рядом с начальником всея киберполиции А. Гринчаком). "По результатам было улучшено методику выявления и идентификации кибер-злоумышленников".
Короче, улучшили и обязательно углубили. Осталось расширить и смазать. Никита, а не западло копам рассказывать как "кибер-злоумышленников" палить?
O
Здравствуйте. Мы ищем специалиста или организацию, который может провести penetration testing приложения с официальным аудитом и сертификацией. Мне посоветовали berezhasecurity, positive testing и российскую компанию Информзащита, но хотелось бы еще пару вариантов. Рассматриваем индивидуальных специалистов, но с возможностью получения сертификата.
Если это важно, компания канадская, вся разработка в Беларуси.
Заранее спасибо.
Если это важно, компания канадская, вся разработка в Беларуси.
Заранее спасибо.
Д
позитивы и необит под санкициями - подумайте, нужны ли вам такие сертификации?)



