GG
Size: a a a
2020 August 25
а, еще раз обернуть все в base64? ну мне тогда со стороны приложения придется это обратно конвертить, странно как-то
В entrypoint.sh раскодируй
A
Принял, посмотрю, спасибо за советы
N
Доброго времени суток! Ребята, пожалуйста, помогите разобраться. У меня в docker-compose.yml:
- docker swarm
- traefik v2.2
- whoami
-gitlab
Все работает хорошо, теперь хотел добавить gitlab, но его не получается даже установить. Контейнер перезагружается каждую минуту, посмотрел логи и не понимаю, как это пофиксить, гугл не помог. То есть создается контейнер и устанавливается гитлаб, во время установки фейлится и снова создается новый контейнер. Добавил конфиг, как с официальной документации gitlab (https://docs.gitlab.com/omnibus/docker/)
- docker swarm
- traefik v2.2
- whoami
-gitlab
Все работает хорошо, теперь хотел добавить gitlab, но его не получается даже установить. Контейнер перезагружается каждую минуту, посмотрел логи и не понимаю, как это пофиксить, гугл не помог. То есть создается контейнер и устанавливается гитлаб, во время установки фейлится и снова создается новый контейнер. Добавил конфиг, как с официальной документации gitlab (https://docs.gitlab.com/omnibus/docker/)
N
version: "3.3"
services:
traefik:
image: "traefik:v2.2"
deploy:
#As the Swarm API is only exposed on the manager nodes, you should schedule Traefik
#on the Swarm manager nodes by default, by deploying Traefik with a constraint on the node's "role"
placement:
constraints:
- node.role == manager
# Make the traefik service run only on the node with this label
# as the node with it has the volume for the certificates
- node.id == uqrjh0tgyq5ncytwdyscmopx9
labels:
- traefik.enable=true
- traefik.docker.network=traefik-public
# Use the custom label "traefik.constraint-label=traefik-public"
# This public Traefik will only use services with this label
# That way you can add other internal Traefik instances per stack if needed
# - traefik.constraint-label=traefik-public
# ROUTER HTTP
- traefik.http.routers.traefik-http.entrypoints=web
- traefik.http.routers.traefik-http.rule=Host(
# ROUTER HTTPS
- traefik.http.routers.traefik-https.entrypoints=websecure
- traefik.http.routers.traefik-https.rule=Host(
#- traefik.http.routers.traefik.entrypoints=web,websecure
# - traefik.http.routers.traefik.rule=Host(
# Define the port inside of the Docker service to use
- traefik.http.services.traefik.loadbalancer.server.port=8080
- traefik.http.routers.traefik-https.tls=true
# Use the "le" (Let's Encrypt) resolver created below
- traefik.http.routers.traefik-https.tls.certresolver=le
# Use the special Traefik service api@internal with the web UI/Dashboard
# - traefik.http.routers.traefik-https.service=api@internal
#
#- "traefik.docker.lbswarm=true"
# Enables Swarm's inbuilt load balancer (only relevant in Swarm Mode).
# If you enable this option, Traefik will use the virtual IP provided by docker swarm
# instead of the containers IPs. Which means that Traefik will not perform any kind of load balancing and will delegate this task to swarm.
command:
- "--log.level=DEBUG"
# Enable the API in insecure mode, which means that the API will be available directly on the entryPoint named traefik.
- "--api.insecure=true"
# Enable the access log, with HTTP requests
- --accesslog
# Enable the Traefik log, for configurations and errors
- --log
# Activates the Swarm Mode (instead of standalone Docker).
- "--providers.docker.swarmMode=true"
# Expose containers by default through Traefik. If set to false, containers that don't
# have a traefik.enable=true label will be ignored from the resulting routing configuration.
- "--providers.docker.exposedbydefault=false"
# ENTRY POINTS
- "--entrypoints.web.address=:80"
- "--entrypoints.websecure.address=:443"
services:
traefik:
image: "traefik:v2.2"
deploy:
#As the Swarm API is only exposed on the manager nodes, you should schedule Traefik
#on the Swarm manager nodes by default, by deploying Traefik with a constraint on the node's "role"
placement:
constraints:
- node.role == manager
# Make the traefik service run only on the node with this label
# as the node with it has the volume for the certificates
- node.id == uqrjh0tgyq5ncytwdyscmopx9
labels:
- traefik.enable=true
- traefik.docker.network=traefik-public
# Use the custom label "traefik.constraint-label=traefik-public"
# This public Traefik will only use services with this label
# That way you can add other internal Traefik instances per stack if needed
# - traefik.constraint-label=traefik-public
# ROUTER HTTP
- traefik.http.routers.traefik-http.entrypoints=web
- traefik.http.routers.traefik-http.rule=Host(
traefik.volkov.club)# ROUTER HTTPS
- traefik.http.routers.traefik-https.entrypoints=websecure
- traefik.http.routers.traefik-https.rule=Host(
traefik.volkov.club)#- traefik.http.routers.traefik.entrypoints=web,websecure
# - traefik.http.routers.traefik.rule=Host(
traefik.volkov.club)# Define the port inside of the Docker service to use
- traefik.http.services.traefik.loadbalancer.server.port=8080
- traefik.http.routers.traefik-https.tls=true
# Use the "le" (Let's Encrypt) resolver created below
- traefik.http.routers.traefik-https.tls.certresolver=le
# Use the special Traefik service api@internal with the web UI/Dashboard
# - traefik.http.routers.traefik-https.service=api@internal
#
#- "traefik.docker.lbswarm=true"
# Enables Swarm's inbuilt load balancer (only relevant in Swarm Mode).
# If you enable this option, Traefik will use the virtual IP provided by docker swarm
# instead of the containers IPs. Which means that Traefik will not perform any kind of load balancing and will delegate this task to swarm.
command:
- "--log.level=DEBUG"
# Enable the API in insecure mode, which means that the API will be available directly on the entryPoint named traefik.
- "--api.insecure=true"
# Enable the access log, with HTTP requests
- --accesslog
# Enable the Traefik log, for configurations and errors
- --log
# Activates the Swarm Mode (instead of standalone Docker).
- "--providers.docker.swarmMode=true"
# Expose containers by default through Traefik. If set to false, containers that don't
# have a traefik.enable=true label will be ignored from the resulting routing configuration.
- "--providers.docker.exposedbydefault=false"
# ENTRY POINTS
- "--entrypoints.web.address=:80"
- "--entrypoints.websecure.address=:443"
N
# Use the custom label "traefik.constraint-label=traefik-public"
# This public Traefik will only use services with this label
# That way you can add other internal Traefik instances per stack if needed
# - "traefik.constraint-label=traefik-public"
# Enable ACME (Let's Encrypt): automatic SSL.
# Email address used for registration. (Required)
- "--certificatesresolvers.le.acme.email=NIKOLAY@gmail.com"
# File or key used for certificates storage. (Required)
- "--certificatesresolvers.le.acme.storage=acme.json"
# KeyType to use (Optional) By default: "RSA4096" (Available "EC256", "EC384", "RSA2048", "RSA4096", "RSA8192")
- "--certificatesresolvers.le.acme.keytype=RSA4096"
# Use a TLS-ALPN-01 ACME challenge. (Optional, recommended)
- "--certificatesresolvers.le.acme.tlschallenge=true"
ports:
- "80:80"
- "8080:8080"
- "443:443" ##Docker sends requests on port 443 to Traefik on port 443
volumes:
# Add Docker as a mounted volume, so that Traefik can read the labels of other services
- /var/run/docker.sock:/var/run/docker.sock:ro
# Mount the volume to store the certificates
- traefik-public-certificates:/_data
networks:
- "traefik-public"
whoami:
image: "containous/whoami"
#If you use a compose file with the Swarm mode, labels should be defined in the deploy part of your service.
deploy:
labels:
# Explicitly tell Traefik to expose this container
- "traefik.enable=true"
# Allow request only from the predefined entry point named "web"
- "traefik.http.routers.whoami-http.entrypoints=web"
# The domain the service will respond to
- "traefik.http.routers.whoami-http.rule=Host(
# Without this a 504 may occur. Defines a default docker network to use for connections to all containers.
- "traefik.docker.network=traefik-public"
# Docker Swarm does not provide any port detection information to Traefik.
# Therefore you must specify the port to use for communication by using the label
- "traefik.http.services.whoami.loadbalancer.server.port=80"
##
- "traefik.http.routers.whoami-https.entrypoints=websecure"
- "traefik.http.routers.whoami-https.rule=Host(
# Make HTTPS route
- traefik.http.routers.whoami-https.tls=true
- traefik.http.routers.whoami-https.tls.certresolver=le
networks:
- "traefik-public"
gitlab:
image: gitlab/gitlab-ce:latest
ports:
- "22:22"
deploy:
placement:
constraints:
- node.id == ps8mhdq5gfw50343agb2v0smm
labels:
- traefik.enable=true
- traefik.docker.network=traefik-public
- traefik.backend=gitlab
- traefik.backend.loadbalancer.swarm=true
- traefik.http.routers.gitlab-http.entrypoints=web
- traefik.http.routers.gitlab-http.rule=Host(
- traefik.http.services.gitlab.loadbalancer.server.port=80
- traefik.http.routers.gitlab-http.service=gitlab
volumes:
- /srv/gitlab/data/:/var/opt/gitlab
- /srv/gitlab/logs/:/var/log/gitlab
- /srv/gitlab/config/:/etc/gitlab
environment:
GITLAB_OMNIBUS_CONFIG: "from_file('/omnibus_config.rb')"
configs:
- source: gitlab
target: /omnibus_config.rb
secrets:
- gitlab_root_password
networks:
- "traefik-public"
gitlab-runner:
image: gitlab/gitlab-runner:alpine
deploy:
mode: replicated
replicas: 4
labels:
- traefik.enable=true
- traefik.docker.network=traefik-public
configs:
gitlab:
file: ./gitlab.rb
secrets:
gitlab_root_password:
file: ./root_password.txt
volumes:
# Create a volume to store the certificates, there is a constraint to make sure
# Traefik is always deployed to the same Docker node with the same volume containing
# the HTTPS certificates
traefik-public-certificates:
# This public Traefik will only use services with this label
# That way you can add other internal Traefik instances per stack if needed
# - "traefik.constraint-label=traefik-public"
# Enable ACME (Let's Encrypt): automatic SSL.
# Email address used for registration. (Required)
- "--certificatesresolvers.le.acme.email=NIKOLAY@gmail.com"
# File or key used for certificates storage. (Required)
- "--certificatesresolvers.le.acme.storage=acme.json"
# KeyType to use (Optional) By default: "RSA4096" (Available "EC256", "EC384", "RSA2048", "RSA4096", "RSA8192")
- "--certificatesresolvers.le.acme.keytype=RSA4096"
# Use a TLS-ALPN-01 ACME challenge. (Optional, recommended)
- "--certificatesresolvers.le.acme.tlschallenge=true"
ports:
- "80:80"
- "8080:8080"
- "443:443" ##Docker sends requests on port 443 to Traefik on port 443
volumes:
# Add Docker as a mounted volume, so that Traefik can read the labels of other services
- /var/run/docker.sock:/var/run/docker.sock:ro
# Mount the volume to store the certificates
- traefik-public-certificates:/_data
networks:
- "traefik-public"
whoami:
image: "containous/whoami"
#If you use a compose file with the Swarm mode, labels should be defined in the deploy part of your service.
deploy:
labels:
# Explicitly tell Traefik to expose this container
- "traefik.enable=true"
# Allow request only from the predefined entry point named "web"
- "traefik.http.routers.whoami-http.entrypoints=web"
# The domain the service will respond to
- "traefik.http.routers.whoami-http.rule=Host(
whoami.volkov.club)"# Without this a 504 may occur. Defines a default docker network to use for connections to all containers.
- "traefik.docker.network=traefik-public"
# Docker Swarm does not provide any port detection information to Traefik.
# Therefore you must specify the port to use for communication by using the label
- "traefik.http.services.whoami.loadbalancer.server.port=80"
##
- "traefik.http.routers.whoami-https.entrypoints=websecure"
- "traefik.http.routers.whoami-https.rule=Host(
whoami.volkov.club)"# Make HTTPS route
- traefik.http.routers.whoami-https.tls=true
- traefik.http.routers.whoami-https.tls.certresolver=le
networks:
- "traefik-public"
gitlab:
image: gitlab/gitlab-ce:latest
ports:
- "22:22"
deploy:
placement:
constraints:
- node.id == ps8mhdq5gfw50343agb2v0smm
labels:
- traefik.enable=true
- traefik.docker.network=traefik-public
- traefik.backend=gitlab
- traefik.backend.loadbalancer.swarm=true
- traefik.http.routers.gitlab-http.entrypoints=web
- traefik.http.routers.gitlab-http.rule=Host(
gitlab.volkov.club)- traefik.http.services.gitlab.loadbalancer.server.port=80
- traefik.http.routers.gitlab-http.service=gitlab
volumes:
- /srv/gitlab/data/:/var/opt/gitlab
- /srv/gitlab/logs/:/var/log/gitlab
- /srv/gitlab/config/:/etc/gitlab
environment:
GITLAB_OMNIBUS_CONFIG: "from_file('/omnibus_config.rb')"
configs:
- source: gitlab
target: /omnibus_config.rb
secrets:
- gitlab_root_password
networks:
- "traefik-public"
gitlab-runner:
image: gitlab/gitlab-runner:alpine
deploy:
mode: replicated
replicas: 4
labels:
- traefik.enable=true
- traefik.docker.network=traefik-public
configs:
gitlab:
file: ./gitlab.rb
secrets:
gitlab_root_password:
file: ./root_password.txt
volumes:
# Create a volume to store the certificates, there is a constraint to make sure
# Traefik is always deployed to the same Docker node with the same volume containing
# the HTTPS certificates
traefik-public-certificates:
N
networks:
traefik-public:
external: true
traefik-public:
external: true
AR
pastebin для неудачников. согласен.
N
Дополнительные файлы:
gitlab.rb:
external_url 'https://gitlab.volkov.club/'
gitlab_rails['initial_root_password'] = File.read('/run/secrets/gitlab_root_password')
nginx['listen_port'] = 80
nginx['listen_https'] = false
letsencrypt['enable'] = false
root_password.txt:
password
gitlab.rb:
external_url 'https://gitlab.volkov.club/'
gitlab_rails['initial_root_password'] = File.read('/run/secrets/gitlab_root_password')
nginx['listen_port'] = 80
nginx['listen_https'] = false
letsencrypt['enable'] = false
root_password.txt:
password
D
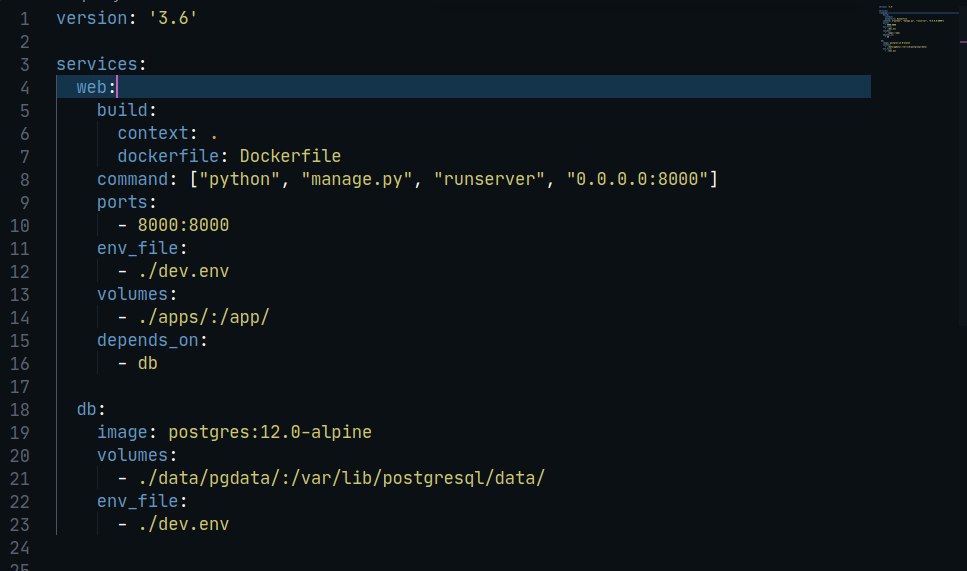
Может кто работал с джанго и может подсказать почему так?
АФ
ты же отдаешь себе отчёт в том, что у тебя command в докер-композ не вяжется с выводом, что у тебя в докерфайле и entrypoint.sh?
D
Александр Фадеев
ты же отдаешь себе отчёт в том, что у тебя command в докер-композ не вяжется с выводом, что у тебя в докерфайле и entrypoint.sh?
почему. ну запускает. миграции и потом сервак. что не так?
AT
это ваще левак какой-то
AF
почему. ну запускает. миграции и потом сервак. что не так?
D
а разница?
AF
а разница?
ну у тебя сначал докерфайл срабатывает, а потом command, кароч скинь докерфайл свой и вот:
web:
build:
context: .
dockerfile: Dockerfile
restart: always
container_name: 'django'
command: bash -c "python manage.py runserver 0.0.0.0:5000"
volumes:
- .:/code
ports:
- '5000:5000'
depends_on:
- db
web:
build:
context: .
dockerfile: Dockerfile
restart: always
container_name: 'django'
command: bash -c "python manage.py runserver 0.0.0.0:5000"
volumes:
- .:/code
ports:
- '5000:5000'
depends_on:
- db
АФ
почему. ну запускает. миграции и потом сервак. что не так?
потому что не запускает сервак
D
ну у тебя сначал докерфайл срабатывает, а потом command, кароч скинь докерфайл свой и вот:
web:
build:
context: .
dockerfile: Dockerfile
restart: always
container_name: 'django'
command: bash -c "python manage.py runserver 0.0.0.0:5000"
volumes:
- .:/code
ports:
- '5000:5000'
depends_on:
- db
web:
build:
context: .
dockerfile: Dockerfile
restart: always
container_name: 'django'
command: bash -c "python manage.py runserver 0.0.0.0:5000"
volumes:
- .:/code
ports:
- '5000:5000'
depends_on:
- db
да я понимаю. ну вот у меня в докерфайле запускается баш скрипт в котором делается migrate. потом срабатывает в компоузе cmd
AF
да я понимаю. ну вот у меня в докерфайле запускается баш скрипт в котором делается migrate. потом срабатывает в компоузе cmd
я тебе написал тело что в command писать