V
Size: a a a
2020 September 19
я ж правильно розумію, що #ifndef і подібні команди впливають тільки на швидкість компіляції?
да и вообще, сама суть сборки файлов в один — такая себе херь
V
поэтому и придумали модули
KS
ну я про #ifndef NDEBUG питаю
V
может, лет через 10 большинство либ на них перейдут)
KS
який дозволяє вставляти блоки коду, якщо режим компіляції == дебаг
KS
типу так, звісно, бібліотеки вставляти через іфндеф - це таке собі діло
V
ну я про #ifndef NDEBUG питаю
не думаю, что сильно влияет
и тебе что важнее, время сборки или качество эксплуатации?
и тебе что важнее, время сборки или качество эксплуатации?
KS
рантайм)
V
так что всё равно нет выбора)
KS
хах, ну так)
🔥
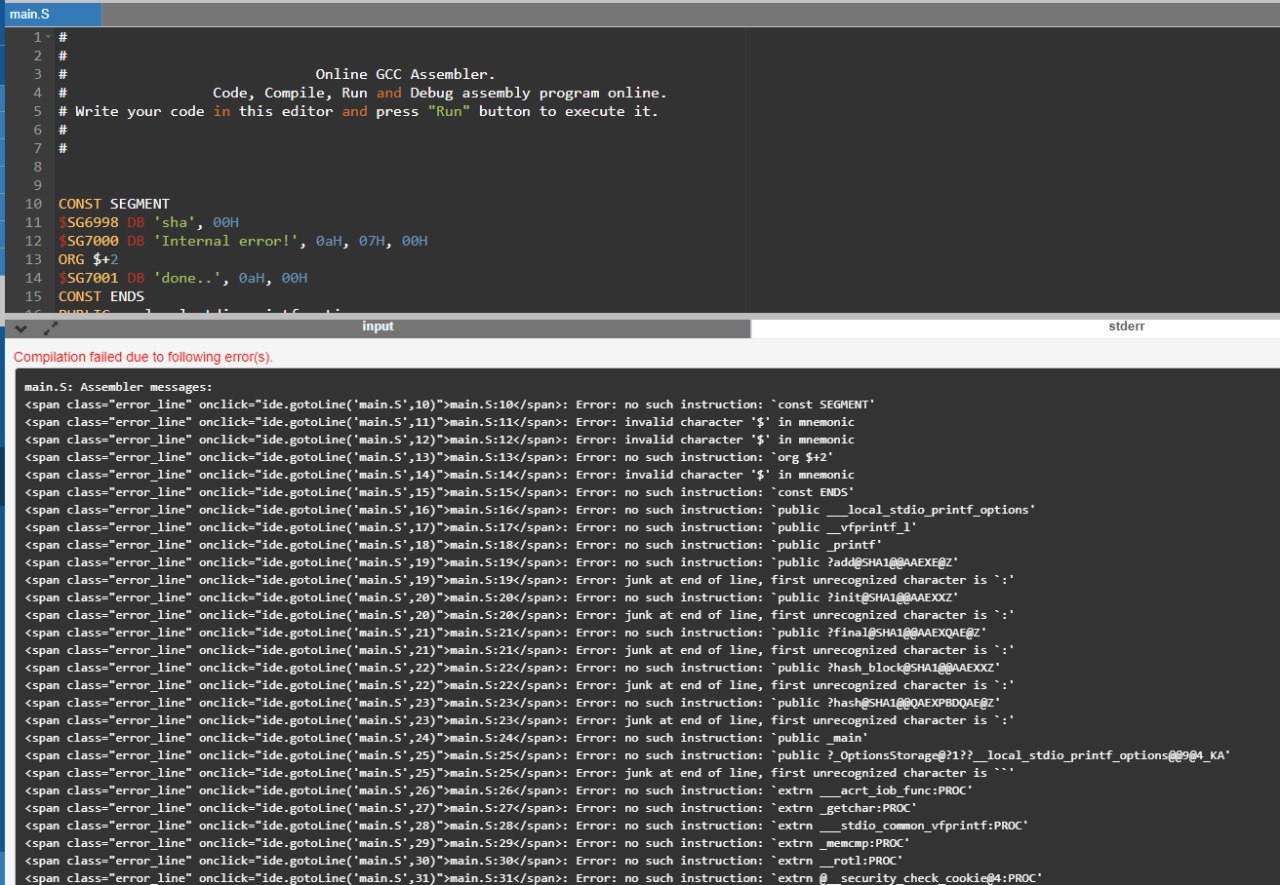
пачаны, нужна помощь:
CONST SEGMENT
$SG6998 DB 'sha', 00H
$SG7000 DB 'Internal error!', 0aH, 07H, 00H
ORG $+2
$SG7001 DB 'done..', 0aH, 00H
CONST ENDS
PUBLIC ___local_stdio_printf_options
PUBLIC __vfprintf_l
PUBLIC _printf
PUBLIC ?add@SHA1@@AAEXE@Z ; SHA1::add
PUBLIC ?init@SHA1@@AAEXXZ ; SHA1::init
PUBLIC ?final@SHA1@@AAEXQAE@Z ; SHA1::final
PUBLIC ?hash_block@SHA1@@AAEXXZ ; SHA1::hash_block
PUBLIC ?hash@SHA1@@QAEXPBDQAE@Z ; SHA1::hash
PUBLIC _main
PUBLIC ?_OptionsStorage@?1??__local_stdio_printf_options@@9@4_KA ; `__local_stdio_printf_options'::`2'::_OptionsStorage
EXTRN ___acrt_iob_func:PROC
EXTRN _getchar:PROC
EXTRN ___stdio_common_vfprintf:PROC
EXTRN _memcmp:PROC
EXTRN __rotl:PROC
EXTRN @__security_check_cookie@4:PROC
EXTRN _memset:PROC
EXTRN ___security_cookie:DWORD
; COMDAT ?_OptionsStorage@?1??__local_stdio_printf_options@@9@4_KA
_BSS SEGMENT
?_OptionsStorage@?1??__local_stdio_printf_options@@9@4_KA DQ 01H DUP (?) ; `__local_stdio_printf_options'::`2'::_OptionsStorage
_BSS ENDS
; Function compile flags: /Odtp
; File C:\Users\Макс\3 курс\kpi_5\kpi_5\re\sha1\sha1_lite.cpp
_TEXT SEGMENT
$T1 = -392 ; size = 348
_res$ = -44 ; size = 20
_test$ = -24 ; size = 20
__$ArrayPad$ = -4 ; size = 4
_main PROC
PH_I_O="v451l3nk0_0l3k511_dmy7r0v1ch"
; 124 : {
00000 55 push ebp
00001 8b ec mov ebp, esp
00003 81 ec 88 01 00
00 sub esp, 392 ; 00000188H
00009 a1 00 00 00 00 mov eax, DWORD PTR ___security_cookie
0000e 33 c5 xor eax, ebp
00010 89 45 fc mov DWORD PTR __$ArrayPad$[ebp], eax
; 125 : assert(sizeof(byte)==1 && sizeof(dword)==4 && sizeof(dword64)==8);
; 126 :
; 127 : byte res[20];
; 128 : byte test[20]={0xd8,0xf4,0x59,0x03,0x20,0xe1,0x34,0x3a,0x91,0x5b,0x63,0x94,0x17,0x06,0x50,0xa8,0xf3,0x5d,0x69,0x26};
00013 c6 45 e8 d8 mov BYTE PTR _test$[ebp], 216 ; 000000d8H
00017 c6 45 e9 f4 mov BYTE PTR _test$[ebp+1], 244 ; 000000f4H
0001b c6 45 ea 59 mov BYTE PTR _test$[ebp+2], 89 ; 00000059H
0001f c6 45 eb 03 mov BYTE PTR _test$[ebp+3], 3
00023 c6 45 ec 20 mov BYTE PTR _test$[ebp+4], 32 ; 00000020H
00027 c6 45 ed e1 mov BYTE PTR _test$[ebp+5], 225 ; 000000e1H
0002b c6 45 ee 34 mov BYTE PTR _test$[ebp+6], 52 ; 00000034H
0002f c6 45 ef 3a mov BYTE PTR _test$[ebp+7], 58 ; 0000003aH
00033 c6 45 f0 91 mov BYTE PTR _test$[ebp+8], 145 ; 00000091H
00037 c6 45 f1 5b mov BYTE PTR _test$[ebp+9], 91 ; 0000005bH
0003b c6 45 f2 63 mov BYTE PTR _test$[ebp+10], 99 ; 00000063H
0003f c6 45 f3 94 mov BYTE PTR _test$[ebp+11], 148 ; 00000094H
00043 c6 45 f4 17 mov BYTE PTR _test$[ebp+12], 23 ; 00000017H
00047 c6 45 f5 06 mov BYTE PTR _test$[ebp+13], 6
0004b c6 45 f6 50 mov BYTE PTR _test$[ebp+14], 80 ; 00000050H
0004f c6 45 f7 a8 mov BYTE PTR _test$[ebp+15], 168 ; 000000a8H
00053 c6 45 f8 f3 mov BYTE PTR _test$[ebp+16], 243 ; 000000f3H
00057 c6 45 f9 5d mov BYTE PTR _test$[ebp+17], 93 ; 0000005dH
0005b c6 45 fa 69 mov BYTE PTR _test$[ebp+18], 105 ; 00000069H
0005f c6 45 fb 26 mov BYTE PTR _test$[ebp+19], 38 ; 00000026H🔥
надо это запустить как-то
🔥
у меня студии нету сейчас, в онлайн компилерах ругает, может кто дать output этого дела?
МЗ
надо это запустить как-то
Через командную строку
🔥
этот код лежал в метаданных картинки) мне засунуть в файл и запустить? какой командой? какой файл?
МЗ
Ну это на ассемблер похоже. Поищи как ассемблер запустить
🔥
да я вот в онлайн компилятор засунул, ругает
МЗ
На что ругает?
JC
is it new perl joke?