Size: a a a
2021 January 12

Опять дженерики https://blog.golang.org/generics-proposal
Теперь уже официальный (опять?) пропозал https://github.com/golang/go/issues/43651
Ну и док пропозала https://go.googlesource.com/proposal/+/refs/heads/master/design/go2draft-type-parameters.md
Теперь уже официальный (опять?) пропозал https://github.com/golang/go/issues/43651
Ну и док пропозала https://go.googlesource.com/proposal/+/refs/heads/master/design/go2draft-type-parameters.md
2021 January 13

Finished dev [unoptimized + debuginfo] target(s) in 15m 21sСобрал я тут тестовое задание на Rust. Теперь можно и посмореть, работает ли.
Я конечно понимаю и уважаю, но ноут придётся заливать водой, он уже 2 минуты продолжает шуметь после компиляции.
Считайте набросом, ватевер.

Иду собесить другого человека (не связанного с постом выше). Что будем-с спрашивать?
Давайте вы поумничаете, а я человека помучаю. :D
А если серьезно, что по вашем было бы важно спросить и до какой глубины копать?
Тестовое было написано хорошо, но не топово. Опыт пару лет, раньше была Java & Groovy, последний год - Go. Что-то там в кубами еще делал.
Давайте вы поумничаете, а я человека помучаю. :D
А если серьезно, что по вашем было бы важно спросить и до какой глубины копать?
Тестовое было написано хорошо, но не топово. Опыт пару лет, раньше была Java & Groovy, последний год - Go. Что-то там в кубами еще делал.

А вот это красиво вообще
2021 January 14

Automated Symbolic Verification of
Telegram’s MTProto 2.0
Within this model, we have provided a
fully automated proof of the soundness of MTProto 2.0’s protocols for first authentication,
normal chat, end-to-end encrypted chat, and re-keying mechanisms with respect to several
security properties, including authentication, integrity, confidentiality and perfect forward
secrecy. These properties are verified also in presence of malicious servers. Our formalization
covers also the behaviour of the users, when relevant; for instance, we have proved that if
the users do not check the fingerprints of their shared keys, a MITM attack is possible.
In the light of these results, we can affirm that MTProto 2.0 does not present any logical
flaw. Vulnerabilities can arise only from the cryptographic primitives, from implementation
flaws (e.g. insufficient checks), from side-channels exfiltration (such as timing or traffic
analysis), or from incorrect user behaviour.
https://arxiv.org/pdf/2012.03141v1.pdf
Telegram’s MTProto 2.0
Within this model, we have provided a
fully automated proof of the soundness of MTProto 2.0’s protocols for first authentication,
normal chat, end-to-end encrypted chat, and re-keying mechanisms with respect to several
security properties, including authentication, integrity, confidentiality and perfect forward
secrecy. These properties are verified also in presence of malicious servers. Our formalization
covers also the behaviour of the users, when relevant; for instance, we have proved that if
the users do not check the fingerprints of their shared keys, a MITM attack is possible.
In the light of these results, we can affirm that MTProto 2.0 does not present any logical
flaw. Vulnerabilities can arise only from the cryptographic primitives, from implementation
flaws (e.g. insufficient checks), from side-channels exfiltration (such as timing or traffic
analysis), or from incorrect user behaviour.
https://arxiv.org/pdf/2012.03141v1.pdf

2021 January 15

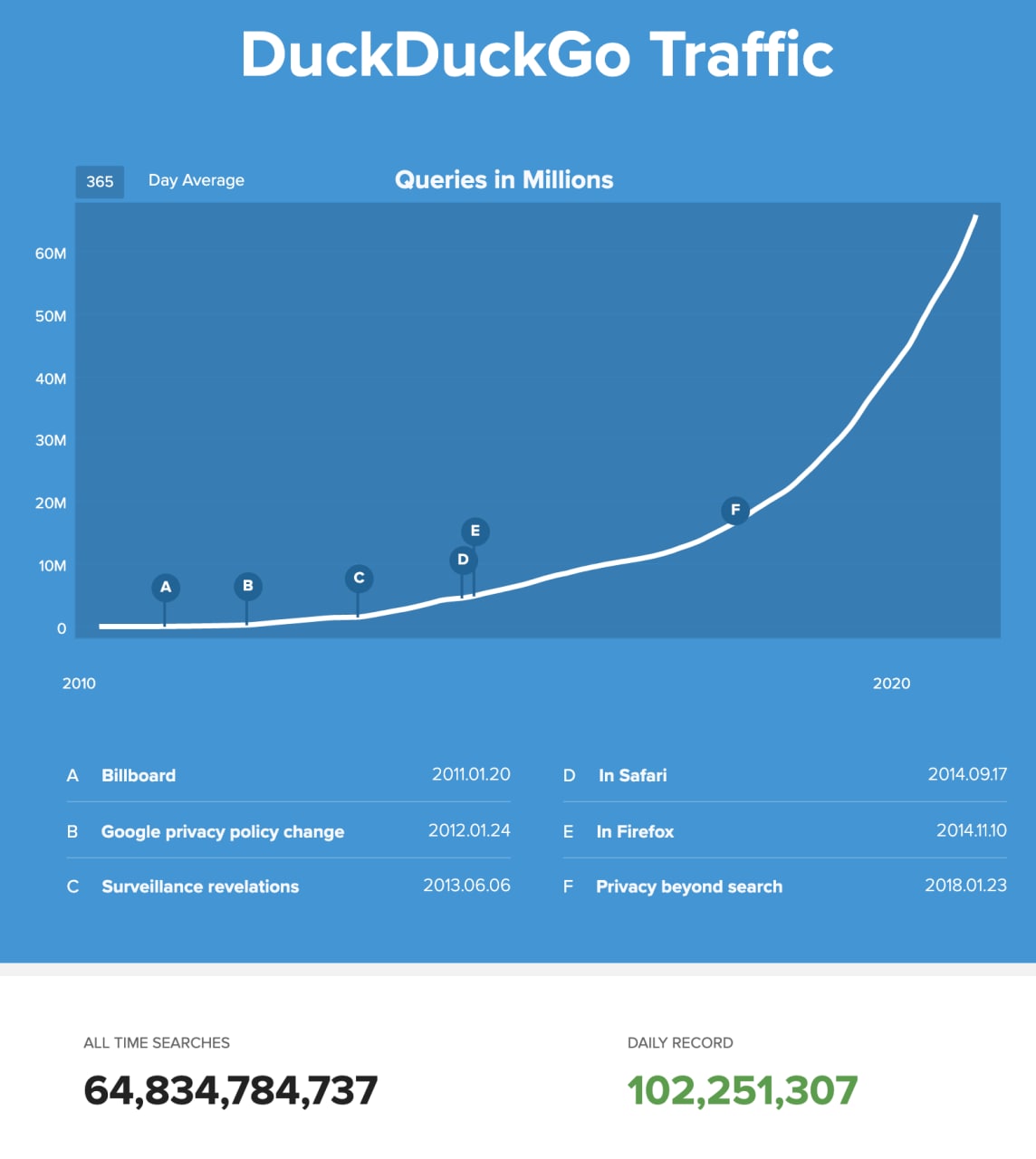
100М в день прошло. https://duckduckgo.com/traffic?lang=en

Когда стартап мутят чуваки, которые любят пилить велосипеды, то всегда можно почитать веселые вещи.
- “So, what database do you use? MySQL, PostgreSQL, SQLite maybe?”, knowing that he loved SQLite.
- “A text file," he replied.
- “Huh?”
- “Yeah, we write out one big JSON object to a text file.”
- “How? When? What?”
Если по теме, они сделали кеширующий клиент для etcd и ловят апдейты на watch-ах. https://github.com/tailscale/tailetc (если так подумать, то напоминает планы Антиреза по Redis и кешированию на стороне клиента (ну а как еще улучшать производительность, когда все дешевые фиксы уже закомичены?))
https://tailscale.com/blog/an-unlikely-database-migration/
- “So, what database do you use? MySQL, PostgreSQL, SQLite maybe?”, knowing that he loved SQLite.
- “A text file," he replied.
- “Huh?”
- “Yeah, we write out one big JSON object to a text file.”
- “How? When? What?”
Если по теме, они сделали кеширующий клиент для etcd и ловят апдейты на watch-ах. https://github.com/tailscale/tailetc (если так подумать, то напоминает планы Антиреза по Redis и кешированию на стороне клиента (ну а как еще улучшать производительность, когда все дешевые фиксы уже закомичены?))
https://tailscale.com/blog/an-unlikely-database-migration/

а так хотелось

HCL приехал, достаточно в конфиге лоадера указать
https://github.com/cristalhq/aconfig v0.10.1
Фидбек приветствуется
".hcl": aconfighcl.New()https://github.com/cristalhq/aconfig v0.10.1
Фидбек приветствуется

Ого, всего лишь 3 года прошло с надежды на релиз го тулзы для проверки зависимостей от Digitalocean
репо https://github.com/digitalocean/gta
пост https://www.digitalocean.com/blog/gta-detecting-affected-dependent-go-packages/
мой комент https://news.ycombinator.com/item?id=15633809
репо https://github.com/digitalocean/gta
пост https://www.digitalocean.com/blog/gta-detecting-affected-dependent-go-packages/
мой комент https://news.ycombinator.com/item?id=15633809
2021 January 16

But Rust’s memory rules aren’t more secure than Node.js’s or Python’s. Your web application written in Rust isn’t going to be systematically more or less secure than an application in Python or Ruby. High-level languages with garbage collectors pay a performance penalty in exchange for generally dodging this whole class of exploits and bugs. You can’t reference uninitialized memory in JavaScript because you simply can’t reference memory-as-memory in JavaScript.
https://macwright.com/2021/01/15/rust.html
Но все же ценность для Edge computing мне кажется недооценена. Хотя готов поверить, что в WASM разница будет не такой и большой. Может у кого-то бенчи есть? я не припоминаю.
https://macwright.com/2021/01/15/rust.html
Но все же ценность для Edge computing мне кажется недооценена. Хотя готов поверить, что в WASM разница будет не такой и большой. Может у кого-то бенчи есть? я не припоминаю.

Может тред по книгам? Что там почитать посоветуете? Думаю можно по любым категориям, чтобы каждый что-то нашел(а).
2021 January 17

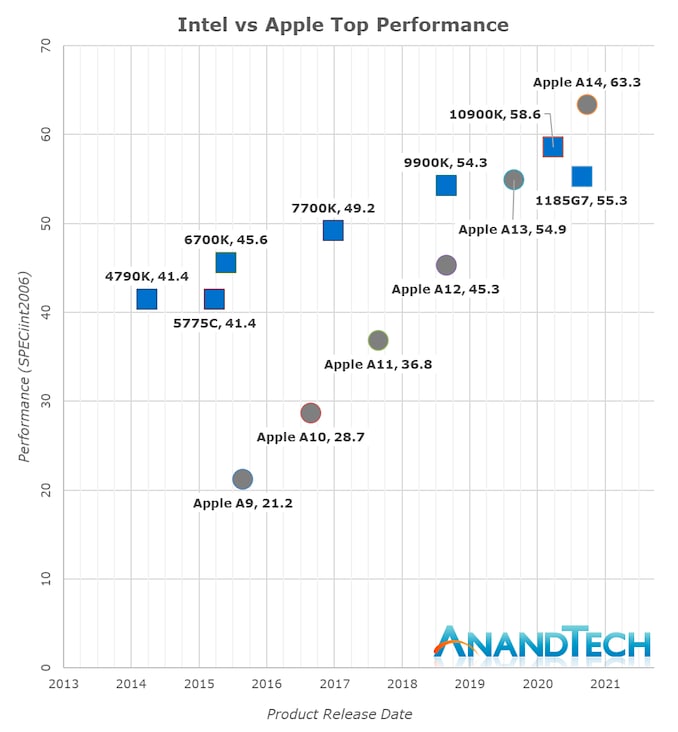
Сложно не восхищаться этим двум линиям

If you indefinitely keep trying to start the container, it could possibly lead to a denial of service on the host. It could be an easy way to do a distributed denial of service attack, especially if you have many containers on the same host. Additionally, ignoring the exit status of the container and always attempting to restart the container likely means the root cause of the container getting terminated will not be investigated.
То есть если я натворил у нас CrashLoopBackOff, то хакер? круто
Проиграл с 10гб Alphine image. А вообще советую весь репорт, там про lifetime контейнеров интересно (50% живет меньше 5мин, вин)
То есть если я натворил у нас CrashLoopBackOff, то хакер? круто
Проиграл с 10гб Alphine image. А вообще советую весь репорт, там про lifetime контейнеров интересно (50% живет меньше 5мин, вин)