F
Size: a a a
2020 June 20
Я училась в гимназии в мск и у нас такого не было. Только в классе девятом поговорили про половые различия. Хотя моя школа была одной из лучших в городе и сотрудничала с мгу
Я тож учился в гимназии в мск, и тоже все было печально. С точки зрения наших учебников, среднестатистический наркоман тогда выглядел полнейшим утырком и ширялся герычем по венам
2020 June 23
ЗБ
хочу купить gygabyte b450m s2h
но мне знакомый говорит что для 7 ядер лучше взять gygabyte b450 aorusm типа там врм лучше и фаз больше,, а если фаз больше значит проц будет лучше разгоняться и лучше будет охлаждение, но я не шарю особо но разница 4к
подскажите кто правый?
но мне знакомый говорит что для 7 ядер лучше взять gygabyte b450 aorusm типа там врм лучше и фаз больше,, а если фаз больше значит проц будет лучше разгоняться и лучше будет охлаждение, но я не шарю особо но разница 4к
подскажите кто правый?
Ты ошибся чатом
С
Ты ошибся чатом
А про что ваш чат ?
D
хочу купить gygabyte b450m s2h
но мне знакомый говорит что для 7 ядер лучше взять gygabyte b450 aorusm типа там врм лучше и фаз больше,, а если фаз больше значит проц будет лучше разгоняться и лучше будет охлаждение, но я не шарю особо но разница 4к
подскажите кто правый?
но мне знакомый говорит что для 7 ядер лучше взять gygabyte b450 aorusm типа там врм лучше и фаз больше,, а если фаз больше значит проц будет лучше разгоняться и лучше будет охлаждение, но я не шарю особо но разница 4к
подскажите кто правый?
для разгона лучше брать с хорошим питанием
A
для разгона лучше брать с хорошим питанием
так я и спрашиваю
стоит ли переплаты в 4к мать гигабайт аорус
там питание лучше?
стоит ли переплаты в 4к мать гигабайт аорус
там питание лучше?
D
так я и спрашиваю
стоит ли переплаты в 4к мать гигабайт аорус
там питание лучше?
стоит ли переплаты в 4к мать гигабайт аорус
там питание лучше?
разгон планируется?
A
для разгона лучше брать с хорошим питанием
или посоветуйте с хорошим питанием тогда
A
разгон планируется?
ну да, 3700х планирую гнать, это же амд
D
ну да, 3700х планирую гнать, это же амд
тогда бери ту что с хорошим врм
A
тогда бери ту что с хорошим врм
ок
а какая с хорошим врм?
gygabyte b450m aorus m подойдёт? там хороший врм?
а какая с хорошим врм?
gygabyte b450m aorus m подойдёт? там хороший врм?
D
насколько я помню аорусы это серия как раз для разгона
A
насколько я помню аорусы это серия как раз для разгона
то есть тогда могу брать любую аорус, если даже она будет дешевле чем я планировал, тк они для разгона
верно?
верно?
Л
насколько я помню аорусы это серия как раз для разгона
..... у гиг б450 врм только у 3-х плат отличается, у всех остальных он абсолютно одинаковый (разве что вариации кондеров отличаются, но учитывая что разгон идет не под ln2, а на повседнев - абсолютно пофиг) для 3700х при его номинальном потреблении без pbo - этого врма за глаза хватит даже в закрытом ящике, с пбо как ни странно тоже на лимитах стандарных хватит, а вот в ручном разгоне при приближении к пределу заметной термоэлектроной миграции потребуется активный обдув радиатора врм, ибо там уже будет 15+ватт) так что что ds3h, что s2x, что s2h, что Gaming X разницы, у аорус только лгбт выходом больше да на самой плате куча бесполезной мишуры и светодиодов)
𝔻
разгон планируется?
разгон райзенов? шта?)))
какое-то время назад интересовался этой темой - там всё грустно в том смысле что они из коробки слегка предразогнанные, и чтобы хоть что-то сверх выдавить - нужны лаб.условия с охлаждением азотом и прочим лерьмом
какое-то время назад интересовался этой темой - там всё грустно в том смысле что они из коробки слегка предразогнанные, и чтобы хоть что-то сверх выдавить - нужны лаб.условия с охлаждением азотом и прочим лерьмом
ЗБ
Attacking the Golden Ring on AMD Mini-PC
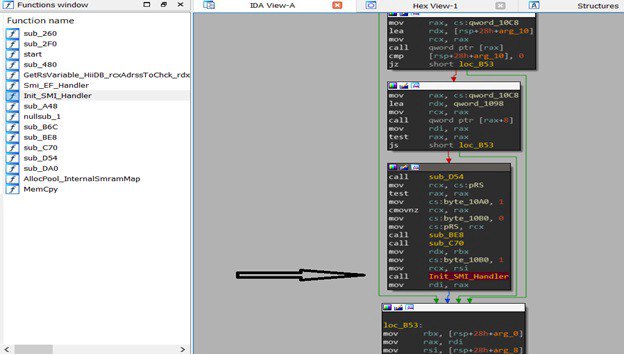
In December 2019 AMD announced a release of a new product line- AMD MiniPc. This MiniPc is actually a direct competition to the well known Intel NUC and Gigabyte Brix. In this post I will show full research and exploitation for 1 of the 3 vulnerabilities I found in the UEFI image and reported to AMD. Specifically speaking all three vulnerabilities reside in SMM (Ring -2) code which is part of the UEFI image. SMM is the most privileged code that can execute on x86 CPU thus allowing to attack any low level component including Kernel and Hypervisor.
The vulnerability in this post allows arbitrary ‘write primitive’ to any location in SMRAM and as consequence execute attacker code in SMM mode. While executing in SMM I will show how it is possible to attack Windows Hypervisor and thus bypass HVCI -hypervisor code integrity. HVCI is a wonderful design and technology which eliminates any chance to run attacker code in Kernel mode. Some think that SMM vulnerabilities are not generic, this is actually not true, there are two major BIOS vendors -AMI and Phoenix that own huge amount of the code in any UEFI image no matter which CPU, Chipset, Motherboard this PC uses. Thanks much to Saar Amar and Alex Matrosov for reviewing the article. Good words also to AMD and ASRock for their fast response and quick fix release.
AMD -2020–0039 — Assigned as CVE-2020–14032; Severity High; 2/4/20 reported; 16/4/20 approved as vulnerability; 8/6/20 fixed version released.
AMD -2020–0040; Severity High; 2/4/20 reported; 16/4/20 approved as vulnerability; Not fixed yet.
AMD -2020–0041; Severity High; 2/4/20 reported; 16/4/20 approved as vulnerability; Not fixed yet.
https://medium.com/@dannyodler/attacking-the-golden-ring-on-amd-mini-pc-b7bfb217b437
In December 2019 AMD announced a release of a new product line- AMD MiniPc. This MiniPc is actually a direct competition to the well known Intel NUC and Gigabyte Brix. In this post I will show full research and exploitation for 1 of the 3 vulnerabilities I found in the UEFI image and reported to AMD. Specifically speaking all three vulnerabilities reside in SMM (Ring -2) code which is part of the UEFI image. SMM is the most privileged code that can execute on x86 CPU thus allowing to attack any low level component including Kernel and Hypervisor.
The vulnerability in this post allows arbitrary ‘write primitive’ to any location in SMRAM and as consequence execute attacker code in SMM mode. While executing in SMM I will show how it is possible to attack Windows Hypervisor and thus bypass HVCI -hypervisor code integrity. HVCI is a wonderful design and technology which eliminates any chance to run attacker code in Kernel mode. Some think that SMM vulnerabilities are not generic, this is actually not true, there are two major BIOS vendors -AMI and Phoenix that own huge amount of the code in any UEFI image no matter which CPU, Chipset, Motherboard this PC uses. Thanks much to Saar Amar and Alex Matrosov for reviewing the article. Good words also to AMD and ASRock for their fast response and quick fix release.
AMD -2020–0039 — Assigned as CVE-2020–14032; Severity High; 2/4/20 reported; 16/4/20 approved as vulnerability; 8/6/20 fixed version released.
AMD -2020–0040; Severity High; 2/4/20 reported; 16/4/20 approved as vulnerability; Not fixed yet.
AMD -2020–0041; Severity High; 2/4/20 reported; 16/4/20 approved as vulnerability; Not fixed yet.
https://medium.com/@dannyodler/attacking-the-golden-ring-on-amd-mini-pc-b7bfb217b437
V
Attacking the Golden Ring on AMD Mini-PC
In December 2019 AMD announced a release of a new product line- AMD MiniPc. This MiniPc is actually a direct competition to the well known Intel NUC and Gigabyte Brix. In this post I will show full research and exploitation for 1 of the 3 vulnerabilities I found in the UEFI image and reported to AMD. Specifically speaking all three vulnerabilities reside in SMM (Ring -2) code which is part of the UEFI image. SMM is the most privileged code that can execute on x86 CPU thus allowing to attack any low level component including Kernel and Hypervisor.
The vulnerability in this post allows arbitrary ‘write primitive’ to any location in SMRAM and as consequence execute attacker code in SMM mode. While executing in SMM I will show how it is possible to attack Windows Hypervisor and thus bypass HVCI -hypervisor code integrity. HVCI is a wonderful design and technology which eliminates any chance to run attacker code in Kernel mode. Some think that SMM vulnerabilities are not generic, this is actually not true, there are two major BIOS vendors -AMI and Phoenix that own huge amount of the code in any UEFI image no matter which CPU, Chipset, Motherboard this PC uses. Thanks much to Saar Amar and Alex Matrosov for reviewing the article. Good words also to AMD and ASRock for their fast response and quick fix release.
AMD -2020–0039 — Assigned as CVE-2020–14032; Severity High; 2/4/20 reported; 16/4/20 approved as vulnerability; 8/6/20 fixed version released.
AMD -2020–0040; Severity High; 2/4/20 reported; 16/4/20 approved as vulnerability; Not fixed yet.
AMD -2020–0041; Severity High; 2/4/20 reported; 16/4/20 approved as vulnerability; Not fixed yet.
https://medium.com/@dannyodler/attacking-the-golden-ring-on-amd-mini-pc-b7bfb217b437
In December 2019 AMD announced a release of a new product line- AMD MiniPc. This MiniPc is actually a direct competition to the well known Intel NUC and Gigabyte Brix. In this post I will show full research and exploitation for 1 of the 3 vulnerabilities I found in the UEFI image and reported to AMD. Specifically speaking all three vulnerabilities reside in SMM (Ring -2) code which is part of the UEFI image. SMM is the most privileged code that can execute on x86 CPU thus allowing to attack any low level component including Kernel and Hypervisor.
The vulnerability in this post allows arbitrary ‘write primitive’ to any location in SMRAM and as consequence execute attacker code in SMM mode. While executing in SMM I will show how it is possible to attack Windows Hypervisor and thus bypass HVCI -hypervisor code integrity. HVCI is a wonderful design and technology which eliminates any chance to run attacker code in Kernel mode. Some think that SMM vulnerabilities are not generic, this is actually not true, there are two major BIOS vendors -AMI and Phoenix that own huge amount of the code in any UEFI image no matter which CPU, Chipset, Motherboard this PC uses. Thanks much to Saar Amar and Alex Matrosov for reviewing the article. Good words also to AMD and ASRock for their fast response and quick fix release.
AMD -2020–0039 — Assigned as CVE-2020–14032; Severity High; 2/4/20 reported; 16/4/20 approved as vulnerability; 8/6/20 fixed version released.
AMD -2020–0040; Severity High; 2/4/20 reported; 16/4/20 approved as vulnerability; Not fixed yet.
AMD -2020–0041; Severity High; 2/4/20 reported; 16/4/20 approved as vulnerability; Not fixed yet.
https://medium.com/@dannyodler/attacking-the-golden-ring-on-amd-mini-pc-b7bfb217b437
зашиваем head в биос, теперь доверенная загрузка на уровне биоса, отламываем ножку, профит